
Today we have another study case which alerted our curiosity. As usual, our software ACSIA is constantly monitoring our server infrastructure and notifying us in real-time of any anomalous activity targeting our servers.
This one is indeed another interesting case therefore let’s not wait long and start immediately looking into the case. Less talk more practice 🙂
Below is the main screenshot where can see the anomaly captured by ACSIA:

We can look in details zooming into the incident captured:

As per incident details we have “Malicious user attack onto web server” originating from IP address 213.159.29.20. The attack is targeting one of our web servers which we use to host demo.acsia.io that we use to store company media posts and videos. The location of attack appears to be originating from Istanbul – Turkey
First thing we take a look at the ownership of the IP address “213.159.29.20”, so we proceed querying that using ACSIA directly:
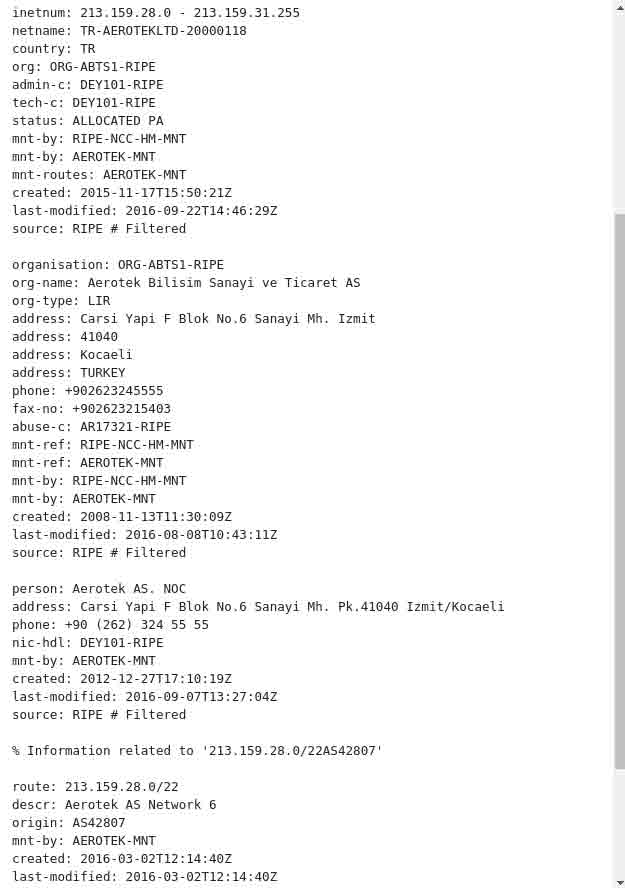
The IP appears to be belong to Aerotek Bilisim Sanayi ve Ticaret AS which is an internet provider located in Turkey in the city of Kocaeli/Izmit.
It is clear enough that the attack is not coming from the provider itself and obvious to us that the geographical location of the attack is not the city of Kocaeli but Istanbul. This is thanks to ACSIA’s accurate geo-locator.

Below we have the email notification that was dispatched in real time by ACSIA:
As outlined in the above screenshots we can also see from the email notification that the attacker was trying to find “phpmyadmin” tool (which we don’t have it by the way) and try to exploit some of its vulnerabilities.
After having verified the identity of the attacker via the IP address we than start our assessment and looking forward to see why this fellow is trying to annoy us:-)
We start with a simple “Nmap” scan to check what we have here and:

Nmap identifies various services running and lists them for us. Most of those services are common services running an almost every server.
What is not common here:
- Port 2049 -NFS (Network file system)
- Port 4242 – mounted (filesystem mounting daemon)
- Port 5432 – Postgresql Database
- Port 8080 – Web application
- Port 9000 – Listener
So the first comes to our mind by looking at those unusually exposed ports is to try the NFS one.
We simply try to mount it to on our local PC by trying to guess the source mount point and…..

That is unbelievable, the entire web application mounted into my PC and I can navigate locally as per highlight in the above screenshot.
Excellent – but I want to dig more on the web app side and see if I can find any login faced pages. We have more ports to analyse there.
We try to look at the “Listener”, the service running on port 9000:

We are making progress here:-)
We have access into the listener but there are some services popping up and impeding us to navigate. That can be drilled down on more but let’s do it the easier way:-)
I said the easier way because knowing that the listener lets you into the process area means that I have higher chances of getting access directly into web app and I am almost sure that the login page is on port 8080.
So let’s tweak the port 8080…

We got the login page, I am going to be generous and won’t disclose the login details here. Long story short, I was able to get in in fairly easy manner

And voila!!!
What we have here is Apache Ambari (https://ambari.apache.org) an application tool stack to manage Apache Hadoop/Hive and several other Big Data components.
The Apache Ambari project is aimed at making Hadoop management simpler by developing software for provisioning, managing, and monitoring Apache Hadoop clusters. Ambari provides an intuitive, easy-to-use Hadoop management web UI backed by its RESTful APIs.
Ambari enables System Administrators to:
- Provision a Hadoop Cluster
- Ambari provides a step-by-step wizard for installing Hadoop services across any number of hosts.
- Ambari handles configuration of Hadoop services for the cluster.
- Manage a Hadoop Cluster
- Ambari provides central management for starting, stopping, and reconfiguring Hadoop services across the entire cluster.
- Monitor a Hadoop Cluster
- Ambari provides a dashboard for monitoring health and status of the Hadoop cluster.
- Ambari leverages Ambari Metrics System for metrics collection.
- Ambari leverages Ambari Alert Framework for system alerting and will notify you when your attention is needed (e.g., a node goes down, remaining disk space is low, etc).
Having obtained full admin access to Ambari I can do whatever I want to these servers where Apache Hadoop is running along other full stack tools.
For instance, let’s check how many servers are hosted on this Hadoop project:

As we can see from the above screenshot, that there are 2 servers hosted each with 16GB of RAM and running the Hadoop stack.
We just click on one of the hosts to see some further information about specific host:

There is lots of information there but the relevant one is about the 3 running services:
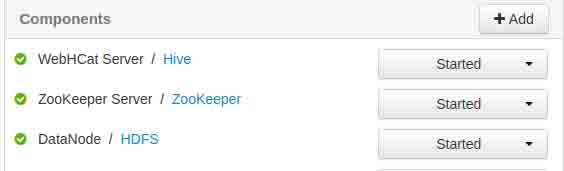
Chat service running on Hive, Zookeeper and HDFS (hadoop filesystem) as data node.
There is some other information that we have not disclosed here and we prefer to keep it that way. But we can give a clue/hint about such information. This Big Data service is run by an IT company that provides internet web services, in particular providing WebChat to more than 10 thousand websites in Turkey.
As mentioned, we generously keep this information but we will contact the IT company and let them know about this case where they jeopardise all those businesses and themselves.
Always keep in mind that this is just one of incident that we pick up randomly and we have 100s of events like this a day attacking our server infrastructures. So I leave it to you to imagine what happens as soon as you expose a server or even a simple service to the public internet. They target you for no reason, these are mass attacks targeting entire subnets and your server/service just happen to be in that subnet.
This is all for now folks.
Happy Hacking!!!