
Today our security product, ACSIA, detected numerous attacks but one in particular took our attention.
The attack originated from Chicago Illinois and it seemed to resolve to a legitimate company called “SecurityScorecard” – www.securityscorecard.com – a security risk rating company.
Usually in the majority of attacks that we see, people launch random and mass attacks onto entire subnets and they mostly do this with the purpose of trying to gain access to server facilities via brute-force attacks.
The reason this attack caught our attention was because this wasn’t a mass attack or random attack as we commonly encounter. In this incident we are dealing with a manual attack where a vulnerability exploitation tool was launched against our server.
Below what ACSIA captured instantly when the attack was in progress in real-time:
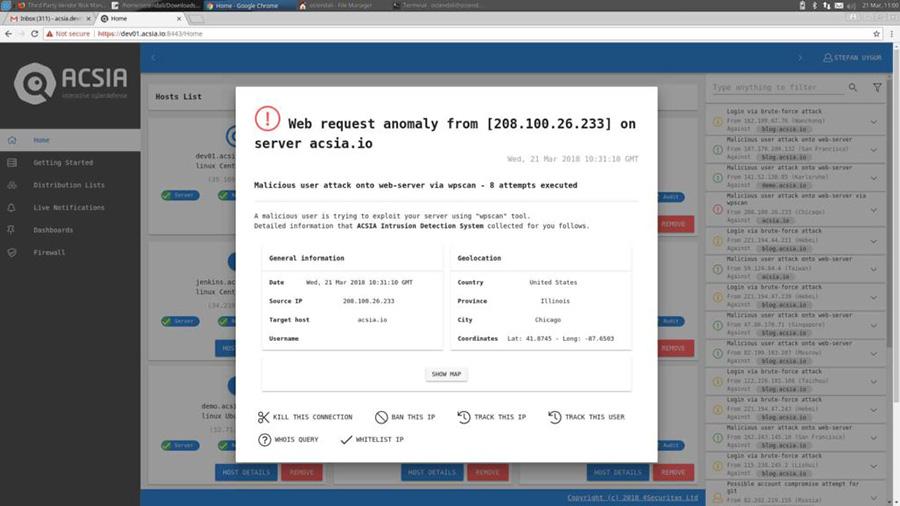
As we can see from the above screenshot, ACSIA, as usual, is very clear in explaining the case. We have a web request anomaly. ‘Anomaly’ because it is not an ordinary request such as visiting the web site but a specific request – with malicious underlying purpose.
If we look into screenshot in detail we see that the tool has been used in the attack is “WPScan” a popular word press vulnerability and exploitation tool and has made 8 attempts to access our server.
Further details provided by ACSIA:

The IP address of attacker including the full geographical location.
Below is the 8 attempts in detail shown by ACSIA again:

We avail of ACSIA’s feature to try to figure out who owns this IP.
Here is the email notification dispatched by ACSIA following the whois record:


The IP address is owned by Steadfast, which is one of the major ISPs/Internet providers in Illinois state. The IP is leased to an organization called Security Scorecard.
So we just wanted to check why a ‘security’ company would run a malicious scan against our server and we hit this web page at first glance.

The web page outputs a message saying “Let us apologize for any inconvenience our scans may have caused you.”.
Well, you can’t just attack someone and then say oh I am sorry if I have caused any harm.
You scanned us, we will then scan you:-)
So we did some further digging to figure out why these friends are trying to perform such scans and to what end. More importantly, if they really are doing this with the purpose they specify in that web page exposed on that IP.
So as we anticipated in the very beginning this IP happened to be owned by company called SecurityScorecard. We dig into their infrastructure and saw that they are hiding behind Cloudflare.
(The majority of IT companies today thinks that the solutions like cloudflare are making their servers safer, to me, they actually help malicious user to hide their tracks:-))
However, lets go back to our digging and investigation. We collected information about their other servers (apart from the web server they have, which hosts their website) and look what we found:

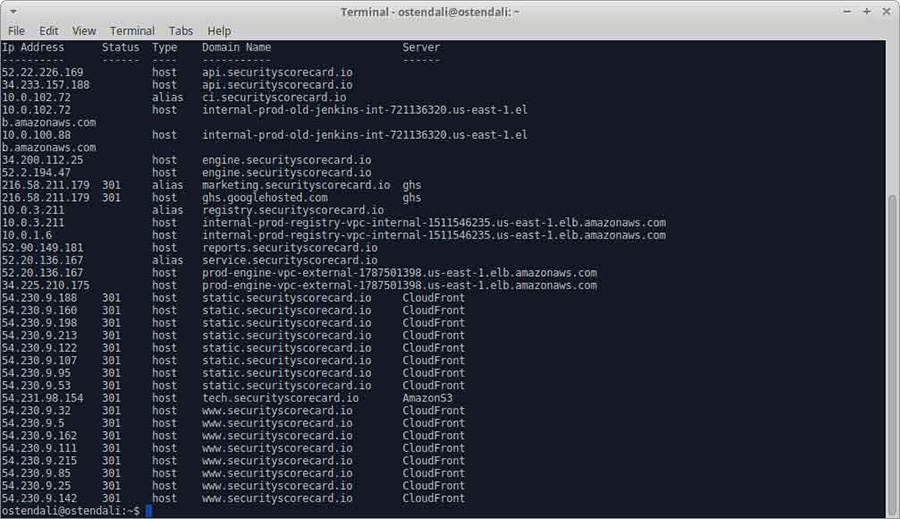
In the above 2 screenshots we clearly see number of servers, including their development and production environments.
For instance, we took a look into one of their domains – “prm1.impartner.com” which redirects to www.impartner.com which happens to be a sort of marketing and business intelligence company. Additionally they have several other portals and companies interrelated to each other (all seems to be owned by the same people). The first thing was coming into my mind to describe this was a sort of interoperating business conglomerate. A ‘full stack’ business chain if you know what I mean.
We did some analysis onto all of their servers (servers ranging from 20 to 25) and we would like to be discrete and keep the detail confidential as we have no bad intentions here. Even though we were attacked by this organization.
We can however, disclose information about one of the servers which we think there is no harm in doing nor any sensitive information is in discussion.
The server in discussion is 45.55.130.194 and this server happen to route us into some info about an employee that currently works with SecurityScorecard.

In the above snippet we just posted the server details including the location and the OS type. It is managed by Luis C.Vargas.
Below is the landing page of the server:
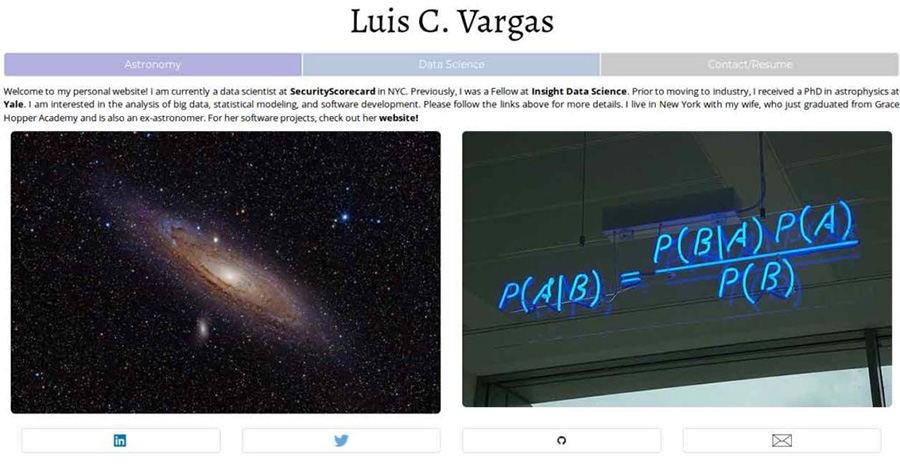
Internet Research Project?
What sort of private company does that sort of research? This sort of disclaimer is used by academic researchers using large anonymised datasets, and those researchers have to outline the nature and purpose of their research and gain the consent of those surveyed where feasible.
This looks like something else – a large data collection operation trying to look legitimate.
In conclusion, we do not want to disclose deep detailed information but the impression we have had based on intel we have is that, this company, or a chain of companies, are set to perform scans against random organisations and individuals for the purpose of collecting information, data scraping in order to create specific profiles and market this data.
Given the coverage of the Facebook data breach, this is particularly topical this week and shines a light on this massive amount of data collection that occurs, sight unseen, online. Facebook itself require their express written permission for automated collection.
We will inform them about this incident and also inform them about the article we are posting here on our blog. Hopefully they will learn their lessons and cease this sort of activity.
Or else, there will be always someone who will bug them:-)
Happy Hacking!!!