A botnet is a number of internet-connected devices, each of which is running one or more bots. Botnets can be used to perform distributed denial-of-service attack (DDoS attack), steal data, send spam, and allow the attacker access to the device and its connection. The owner can control the botnet using command and control (C&C) software.
From Dublin to Austria to a suburb of a city in North Eastern China, we bring you a recent investigation of online botnets. During our development and testing phase of ACSIA, our automated cyberdefense product we activated several testing servers exposed to the public internet. This is deliberate and our exposed servers are constantly subject to multiple random attacks (botnet, script kiddies, random hackers and so on) as an hourly occurrence. These attackers are mostly automated and attempt to gain control of computers and devices which are open to the web.
Our product alerts us with email notifications in real-time for important/relevant security issues and threats. From time to time we pick out unusual cases for further investigation.
One of the email notifications we received is shown here:
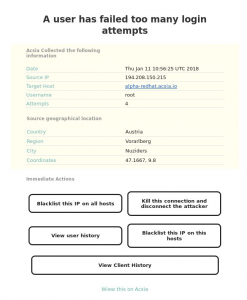
We don’t usually investigate bot net attacks as in majority they originate from automated botnets in geographical locations outside US and EU. However as we see from the above notification the source is located in Nuziders – Austria.
This has sparked our curiosity and we decided to dig into this case.
To learn more we performed some very basic security tests and information gathering to have some further details about why an EU resident – subject to GDPR and national data and security regulations would attempt such an obvious attack.
The source turned out to be a regional Austrian ISP and cable TV company which provides customers with internet connection.

One of their IP’s was attempting to brute force our servers and gain access to our systems.
Further detective work
So why in 2018 would an ISP from a regional Austrian ISP be launching brute force attacks on a newly commissioned server located in Dublin?
Well, it turned out that things got a little stranger. Using some security and infrastructure tools we were able to determine that the source of the attack arose not from Austria, not even from within Europe but from a source in China.

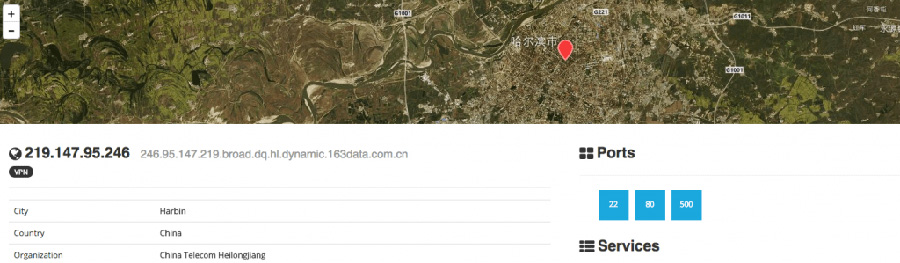
Geo-IP (courtesy of Shodan)
The Austrian device was actually being controlled by another device based in the city of Harbin in North East China.
What we did next
We informed the Austrian ISP about this device on their network, and also sent a note to China Telecom. We have not heard back from either to date…..
Threats and trends
A botnet attack can be devastating. In 2016 the Mirai botnet affected large parts of the internet, including Twitter, Netflix, CNN, and other major sites, as well as major Russian banks and the entire public internet of Liberia. The botnet took advantage of unsecured internet of things (IoT) devices installing malware that then attacked servers that route internet traffic. Mirai infected vulnerable devices that used default user names and passwords and is still affecting devices worldwide to this day.
Bot nets enable hackers to steal bank credentials and website cookies to impersonate victims, searching hard disks for specific files, granting threat actors remote access to a computer, and allowing threat actors to exfiltrate stolen information or download additional malware.The botnet-as-a-service model has grown increasingly popular. Threat actors rent subsets of their botnets for malicious activities such as distributed denial of service (DDoS) attacks, click fraud, cryptocurrency mining, and targeted attacks.
The ISP’s above likely were compromised by groups to be instrumental in attacking EU based entities. Having a compromised EU located device is a big plus to a criminal organisation.
IoT Threats
There is a great deal of hype about IoT, Smart Homes and connecting all devices in our daily life to the public internet. Security is rarely a top consideration. Most IoT devices have very basic security controls and are easily compromised. IOT devices are cheap and mass produced with little built in security or updates planned into their functional life.
As consumers continue to buy low-cost, insecure devices, the number of vulnerable end points (like the IP’s above) just keeps going up. Gartner estimates that there will be 8.4 billion connected devices in use by the end of this year, and that will more than double by 2020, to 20.4 billion.
This simple random case how systems can be compromised by 3rd parties masquerading as legitimate actors and this threat is proliferating.
The complex, interconnected networks that cloud providers have developed can create a single point of failure for hundreds of businesses, including government entities, critical infrastructures, and essential healthcare organisations. Cybercriminals are capitalising on this situation to devise hard-to-detect attacks that can disrupt cloud providers and their customers.
Will 2018 be the the year that the industry wakes up, and device manufacturers, regulators, telecom companies, and internet infrastructure providers work together to isolate compromised devices, take them down or patch them, to ensure that automated bot nets can no longer proliferate? We are not holding our breath….